Automated Testing with iSEC’s SecurityQA Toolbar :
The process for testing for injection flaws in web applications can be cumbersome and
complex across a big web application with many forms. To ensure that the web application
gets the proper security attention, iSEC Partners’ SecurityQA Toolbar provides a feature to
test input fields on a per-page basis rather than having to scan the entire web application.
While per-page testing may take a bit longer, it can produce strong results since the testing
focus is on each page individually and in real time. To test for injection security issues,
complete the following steps.
1. Visit www.isecpartners.com and request an evaluation copy of the product.
2. After installing the toolbar on Internet Explorer 6 or 7, visit the web application
using IE.
3. Within the web application, visit the page you want to test. Then choose Data
Validation | SQL Injection from the SecurityQA Toolbar (Figure 1-1).
4. The SecurityQA Toolbar will automatically check for SQL Injection issues on
the current page. If you want to see the progress of the testing in real time,
click the expand button (the last button on the right) before selecting the SQL
Injection option. The expand button will show which forms are vulnerable to
SQL Injection in real time.
5. After the testing is completed on the current page, as noted in the progress bar
in the lower left side of the browser, browse to the next page of the application
(or any other page you wish to test) and repeat step 3.
6. After you have completed SQL injection testing on all desired pages of the
web application, repeat steps 3 and 5 for LDAP Injection, XPATH Injection, OS
Commanding, or any other injection testing under the Data Validation menu.
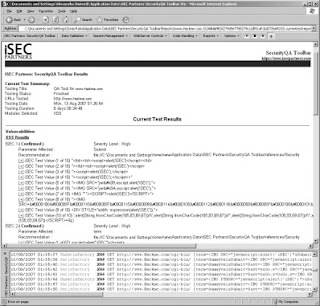
7. Once you have finished testing all of the pages on the web application, view
the report by selecting Reports | Current Test Results. The SecurityQA Toolbar
will then display all security issues found from the testing. Figure 1-2 shows
a sample injection report. Notice the iSEC Test Value section that shows the
specific request and the specific response in boldface type, which shows which
string triggered the injection flaw.